Identity verification is one of those areas that rarely breaks loudly. When it fails, it does not usually bring systems down or trigger immediate incidents. Instead, it creates quiet risk. Risk that accumulates in data stores, access patterns, and undocumented assumptions, until one day it surfaces during an audit, a partner review, or a regulatory inquiry.
This case study explores how INSART approached Plaid Identity integration for a fintech platform that had already implemented identity checks, but lacked the architectural rigor required to make those checks secure, auditable, and defensible over time.
The goal was not simply to verify users. The goal was to build an identity system the company could stand behind under scrutiny.
Client Context
The client was a regulated fintech platform operating in an environment where identity data was required for onboarding, compliance, and ongoing risk management. Identity verification was tied directly to regulatory obligations and internal policies, not just fraud prevention.
Plaid Identity had been introduced earlier in the product lifecycle, primarily to satisfy immediate onboarding requirements. The integration worked functionally, and users were able to complete identity checks. However, as the company grew and expectations increased, it became clear that identity verification could no longer be treated as a supporting feature embedded inside onboarding logic.
Identity had become infrastructure.
Initial Situation
At the time INSART joined, identity data existed in the system, but it lacked clear ownership. Some validation occurred client-side. Some Plaid responses were trusted implicitly. Backend checks existed, but they were incomplete and inconsistent.
Sensitive PII was stored alongside general application data, increasing the risk surface. Access controls were present, but not enforced uniformly across services. Logs existed, but they were not structured in a way that could support an audit trail.
Most concerning was the inability to confidently answer fundamental questions, such as how a specific user’s identity had been verified, who had access to that data, and how long sensitive information was retained.
The system worked operationally, but it was not audit-ready.
Reframing Identity as a Compliance Boundary
INSART began by reframing how identity verification was understood within the platform.
Rather than viewing Plaid Identity as an onboarding step, we treated it as a compliance boundary. This meant acknowledging that identity data required different handling rules, different storage guarantees, and different access patterns than standard product data.
Once this framing was agreed upon, it became clear that the existing integration could not simply be patched. Identity needed to be separated, isolated, and formalized as its own domain.
Core Technical Challenges
Several challenges emerged immediately once identity was treated as regulated data.
The platform needed a secure way to handle highly sensitive PII without leaking it into logs, analytics, or downstream services. Identity validation had to be performed on the backend, without trusting the client or exposing raw responses. Data storage had to align with compliance expectations around encryption, access control, and retention.
At the same time, the system needed to be audit-ready. That meant traceability, immutability of records, and clear evidence of how identity decisions were made.
Solving any one of these in isolation would not be sufficient. The solution had to be cohesive end to end.
Designing a Dedicated Identity Architecture
INSART introduced a dedicated identity domain within the backend architecture. Identity data was no longer treated as part of the user profile or onboarding flow. Instead, it became a separate subsystem with its own lifecycle and guarantees.
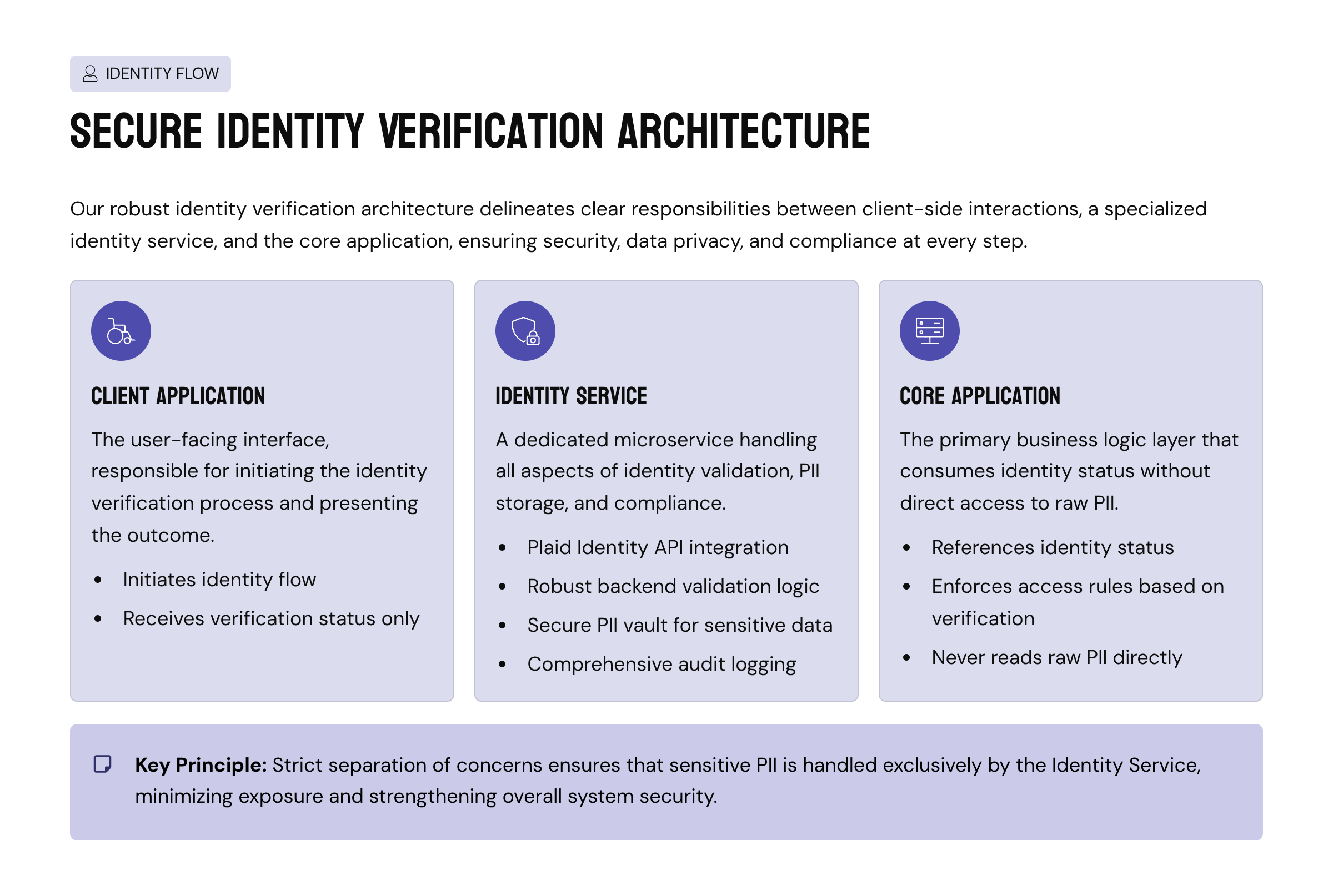
Diagram: Identity System Architecture
Client Application
→ initiates identity flow
→ receives verification status only
Identity Service
→ Plaid Identity API
→ backend validation logic
→ PII vault
→ audit logging
Core Application
→ references identity status
→ enforces access rules
→ never reads raw PII
This separation ensured that the core application could make decisions based on identity status without ever handling sensitive data directly.
Backend-Driven Identity Validation
INSART redesigned the identity flow so that the backend became the sole authority on identity verification.
When a user completed the identity flow, Plaid Identity responses were received and validated server-side. Rather than persisting raw responses indiscriminately, the backend extracted only the fields required for compliance and verification, mapped them to internal states, and discarded anything unnecessary.
The client application received only high-level outcomes, such as verified, pending, or failed. No sensitive identity fields were ever returned to the client.
This approach dramatically reduced the risk of accidental exposure and ensured that identity decisions were explainable and repeatable.
Secure Handling and Storage of PII
PII was treated as a restricted asset with strict architectural constraints.
INSART introduced a dedicated PII vault, isolated from the main application database. All identity data was encrypted at rest and in transit. Access was limited to a narrow set of backend services, each operating under the principle of least privilege.
Diagram: Data Separation Model
User Table
→ identity_status
→ verification_timestamp
PII Vault
→ encrypted identity attributes
→ access-controlled
→ audit-logged
By separating sensitive data structurally, the platform eliminated entire classes of accidental exposure that often arise from shared schemas or convenience joins.
Controlled Backend Access and Least Privilege
INSART ensured that only explicitly authorized backend components could access identity data. Developers working on unrelated parts of the platform never needed access to PII. Support teams could resolve user issues using identity status indicators rather than raw data.
This approach reduced operational risk and made internal access reviews straightforward. Security was enforced by architecture, not by reminders or documentation alone.
Audit Logging and Traceability by Design
Audit readiness was built into the system from the start.
Every identity-related event was logged in a structured, immutable format. This included identity submissions, verification outcomes, access to PII, and changes in verification status. Each log entry captured who initiated the action, when it occurred, and what the outcome was.
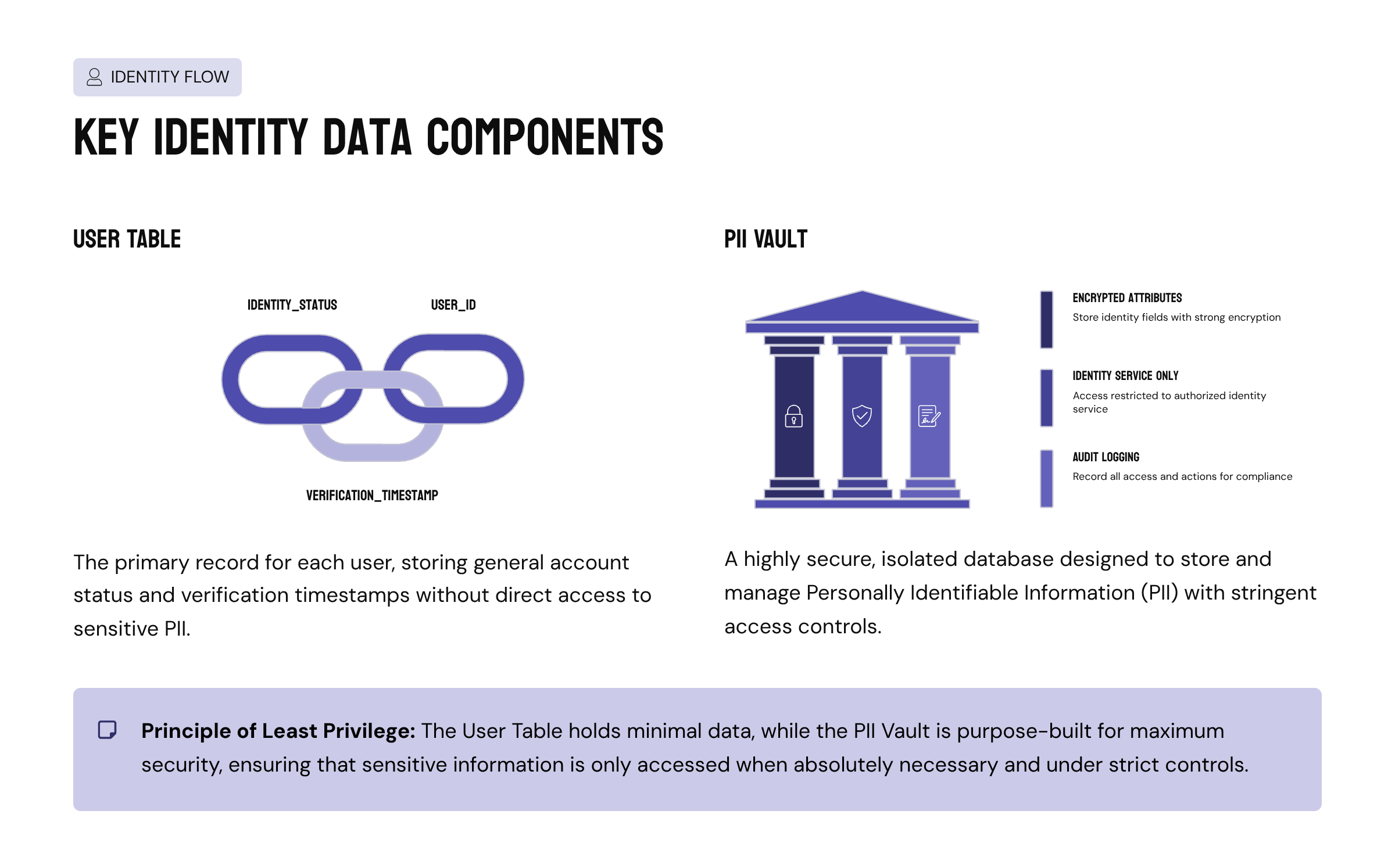
Diagram: Identity Audit Trail
Identity submission
→ verification response
→ status assignment
→ access events
→ retention lifecycle
This made it possible to answer audit questions without reconstruction or guesswork.
Documentation for Compliance and Risk Teams
INSART delivered comprehensive documentation alongside the implementation. This documentation was designed not for engineers alone, but for compliance and risk stakeholders.
It explained identity data flows, storage and retention policies, access control models, and incident response procedures. By making the system understandable, INSART reduced friction between engineering and compliance teams and accelerated future reviews.
Outcome
After implementation, identity verification became compliance-ready and secure by design. Sensitive data was clearly owned, isolated, and protected. Regulatory risk was reduced significantly.
Audits became manageable rather than stressful. Engineering teams gained confidence working around identity features without fear of accidental exposure. Most importantly, the platform established a clear, defensible identity layer that could evolve alongside regulatory expectations.
Closing Thought
Identity verification is one of the most sensitive responsibilities a fintech platform carries. When treated casually, it becomes a long-term liability. When designed deliberately, it becomes a foundation of trust.
INSART’s approach to Plaid Identity emphasizes security, compliance, and architectural discipline. This case study demonstrates how identity verification can be built not just to pass today’s checks, but to withstand tomorrow’s scrutiny.





